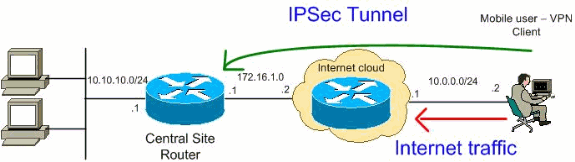
Remote-access VPNs allow secure access to corporate resources by establishing an encrypted tunnel across the Internet. It allows organizations to cost-effectively and securely extend the reach of their networks to anyone, anyplace, anytime.
There are two primary methods for deploying remote-access VPNs: IP Security (IPsec) and Secure Sockets Layer (SSL).
We can create IPsec and SSL vpn on a perimeter router or Firewall.
Here I am introdusing an Ipsec based remote access vpn on configuration Cisco IOS router.
( These are only basic configurations, firsly I introdused with a Dynamic-map based configuration and
the preceeding sessions will include VTI base VPNS , CA Base VPNs and so on)
Remote Access VPN Configuration
Configurin Cisco IOS remote-access vpn
aaa new-model
aaa authentication login LOCAL_AUTH local
aaa authorization network LOCAL_NET local
username cisco password 0 cisco123
crypto isakmp policy 3
encr 3des
authentication pre-share
group 2
hash md5
crypto isakmp client configuration group vpnclient
key cisco
pool ippool
crypto ipsec transform-set myset esp-3des esp-md5-hmac
crypto dynamic-map dynmap 10
set transform-set myset
reverse-route
crypto map CLIENT_MAP client authentication list LOCAL_AUTH
crypto map CLIENT_MAP isakmp authorization list LOCAL_NET
crypto map CLIENT_MAP client configuration address respond
crypto map CLIENT_MAP 10 ipsec-isakmp dynamic dynmap
interface Ethernet0/0
ip address 10.10.10.1 255.255.255.0
crypto map CLIENT_MAP